
We know that blockchain wallet features are becoming increasingly sophisticated, but most consumers don’t know the significance of these security features. Here’s what you need to know.
Table of Contents
- What is a blockchain wallet?
- What is a hardware wallet?
- How do SecuX’s blockchain wallets work?
- Why choose a SecuX blockchain wallet?
- How can I transfer crypto to my SecuX blockchain wallet?
Scams and hacks are not new to the cryptocurrency industry. In fact, 2021 saw a record $14 billion in cryptocurrency stolen or scammed from investors, according to Chainalysis data.
With crypto criminals finding more and more clever ways to take others’ digital assets, it is prudent to fully understand the purpose of blockchain wallet security and features.
Our experience in the cryptocurrency cold storage space has led us to design the best blockchain wallet in the marketplace. Below, we’ll explain how these security features work and what went into our design decisions.
What is a blockchain wallet?
Firstly, we should define what a blockchain wallet is and its importance to the cryptocurrency ecosystem.
When you buy crypto, you don’t receive any physical currency. The crypto you purchase is stored digitally on the currency’s blockchain itself. What you, the cryptocurrency owner, receive is a blockchain wallet address, a public key, and a private key.
The wallet address described above refers to a particular location on the blockchain. Only you know that this address belongs to you. The contents of this address reflect your current holdings as you buy, earn, and spend crypto. The public key and private keys are linked to this address.
You may send others your public blockchain address to receive crypto from them. You will use your private key to send your crypto to others.
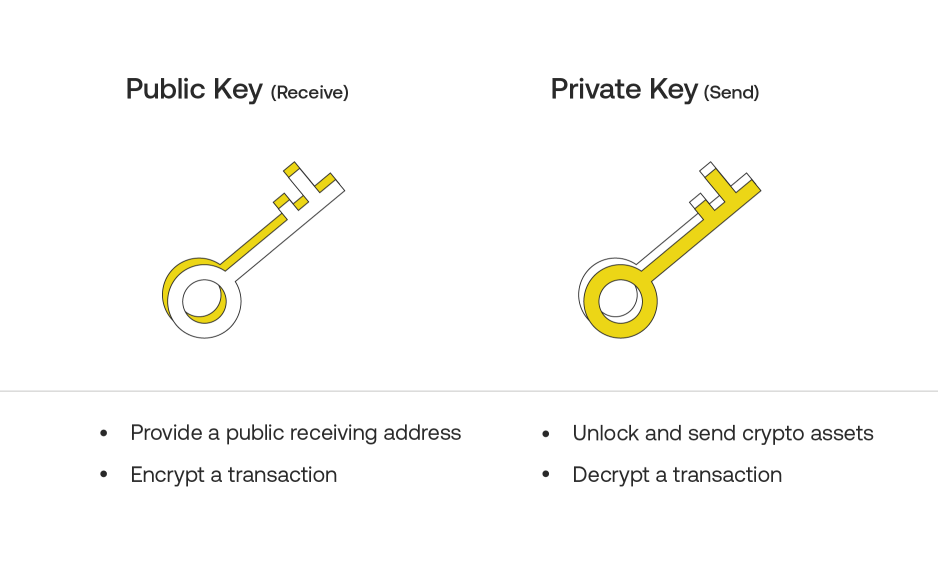
Cryptography via advanced mathematics guarantee that your address and the two keys cannot be linked with each other and back to you specifically by outsiders.
However, there is inherent risk to managing your private keys that are linked to your blockchain address. Your ability to access your crypto depends entirely on your keys and your access to them.
If you lose your private keys, or if someone else comes to know what your keys are, you can lose your crypto for good. Neither the cryptocurrency creator, nor law enforcement, nor the government can guarantee the recovery of your crypto assets.
This makes it very important to keep your keys secure. So how can you do this?
One solution is to store your keys on an exchange (like Coinbase) where you purchase your crypto. But if you do this, you are at the mercy of the exchange. If attackers hack the exchange and steal your keys, you may have your crypto stolen from you.
This is where blockchain wallets come in. The wallet holds your keys!
Crypto wallets may be stored online, which are called “software wallets” or they may be stored offline, which are called “hardware wallets”. For more on the difference between the two, be sure to check out our previous blog post.
If you store your keys at the exchange, you are basically using the exchange’s online wallet. In this article, we look at hardware wallets. Specifically, we will examine SecuX’s hardware wallets.
What is a hardware wallet?
A hardware wallet, also known as a cold wallet, is a physical device designed to securely store private keys for cryptocurrency transactions. Unlike a software wallet, which can be vulnerable to hacking and cyber-attacks, a cold wallet is kept offline for added safety and security. To use a hardware wallet, you simply connect it to your computer or mobile device to access your private keys. The keys themselves never leave the device, giving you complete control over your crypto wallet. If you lose your hardware wallet, additional layers of security such as a PIN or OTP ensure that no one else can access your keys. SecuX offers a range of hardware wallet options to meet your security and storage needs, providing a secure and reliable solution for storing your crypto assets.
How do SecuX’s blockchain wallets work?
Our blockchain wallets are easy to use, but are steeped in security. This makes them accessible to cryptocurrency investors of all levels of maturity.
After setting up the device, you can connect with it using your computer or mobile device (iOS or Android). This will allow you to subsequently send or receive crypto using your wallet.
Why choose a SecuX blockchain wallet?
Our cryptocurrency wallets have incorporated security into each aspect of their design and function. Let’s look at some specific features and support offerings that make us cryptocurrency’s best blockchain wallet in 2022 and beyond.
Secure Element (SE) chip
Our blockchain wallets use the Infineon SE Chip, which is German-manufactured and provides military-grade security, to store the private key and your wallet PIN. Its firmware supports a fixed API which specifically does not query for the keys.
The SE chip in our wallets monitor and detect any attempts to tamper with the device. If it believes that an intruder is attempting to access it, it has an integrated self-destruct mechanism that will delete all of the data on the device.
This sensitive data will never leave the chip under any circumstance.
PIN Protection
You must use a PIN to access your SecuX wallet–regardless of which model you choose.
The wallet allows only 5 attempts to enter the correct PIN. If the number of login attempts is exceeded, the wallet resets itself to factory settings. To then access it, you will need to use your Recovery Words to regenerate the keys.
Compatibility with BIP 32, 39, and 44
Our blockchain wallets are compatible with Bitcoin Improvement Proposal (BIP) standards. This allows you to regenerate your crypto keys using the 24 recovery words that you specified when you first set up the wallet.
This is very useful if you misplace, damage, or lose your device. You can get a new device and use the same Recovery Words to create the same keys and regain control of your cryptocurrency assets.
Bluetooth Authentication
When you connect to your device over Bluetooth, you will need to go through three layers of security:
- PIN to unlock the SecuX wallet
- Password to login to the SecuX app
- An OTP to pair with the device Bluetooth
This enhances the safety of your keys!
Hidden wallet
SecuX allows you to create a hidden wallet using a 25th Recovery Word, called a passphrase.
The hidden wallet has a different PIN, and requires the final passphrase in addition to the original 24 recovery words. This helps in cases where all other aspects of the security measures have been breached by allowing you to keep part of your crypto holdings in the hidden wallet.
As the owner, you can access the hidden wallet easily using its PIN.
Learn more about the Hidden Wallet feature.
Sleek, simple user interface
On top of our vault-like security measures, SecuX is known for its clean design and intuitive interface.
Did you know that it can also be used to store over 1000 different crypto coins and tokens?
We have our own dedicated apps found on the iOS App Store, the Google Play Store for Android devices, and even our own web application!
If you ever have any issues, our dedicated customer support team is standing by to quickly assist.
How can I transfer crypto to my SecuX blockchain wallet?
Transferring crypto to your SecuX wallet is simple! You can use your wallet with a web, iOS, or Android device application to receive crypto in three steps:
- Generate the address to receive the crypto (you can do this offline on the device, or by connecting the device via laptop or mobile)
- Send the address to the sender as a QR code
- Check the account balance to verify receipt of the crypto
For more details on sending and receiving cryptocurrency on a SecuX device, please choose from the available applications here.
As you can see, we’ve invested many resources into designing security functions for SecuX blockchain wallet devices. It’s our duty to provide you with vault-grade blockchain security products to manage your private keys and crypto assets, so you can have peace of mind.
Have any questions or would like to get in contact with a team member? Feel free to contact us today!
0 comments