
Written by: Jess Lin
Contributor: Andy Chen
Disclaimer: The information provided in this article is for educational purposes only and should not be considered as financial advice.
There is some math in the crypto world and it isn’t just coding skills that provide robust digital security. Cryptographic hash can transform an input of any size into a unique, fixed-length output. It’s an action that’s based on logic and computation. Even the slightest change to the input creates a dramatically different output. This is a feature that enhances data integrity in our ever-evolving digital universe.
The name may allude to it but it’s really not that cryptic. Let’s demystify crypto hash!
Understanding Cryptographic Hash Functions and Types
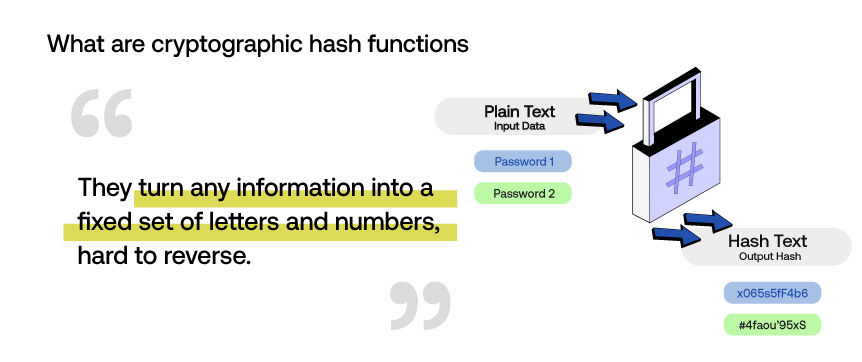
Cryptographic hash functions are like secret codes in the digital world. They take any information and turn it into a set length of letters and numbers, no matter how big or small the original information is. What’s really interesting is that even a tiny change in the original data creates a completely different code.
This feature is great for keeping data safe, as it is easy to create the code from the data, but very hard to go backwards and figure out the original data from the code. This is commonly used in blockchain technology.
Let’s take a closer look at the different types of cryptographic hash functions.
MD5
This type of hash function is short for ‘Message Digest Algorithm 5’. MD5 is a common cryptographic hash function that generates a 128-bit hash value (the result of the hash function). It can be said that MD5 is one of the oldest types of cryptographic hash functions. In the earlier days of web2, MD5 played a critical role in verifying data integrity.
In terms of blockchain, MD5 was initially used in proof-of-work (PoW) systems (old Ethereum v1 and Bitcoin) due to its speed, but this is no longer. MD5 is no longer used because it is susceptible to hash collisions, where different inputs produce the same hash value, which can harm the integrity and security of blockchain transactions.
SHA-1
SHA-1 is short for ‘Secure Hash Algorithm 1’, and this hash function generates a 160-bit hash value. It is considered more secure than MD5. However, SHA-1 has now been deemed insecure due to weak collision resistance. SHA-1 isn’t used in modern blockchain systems for the same security reasons as MD5, but understanding its weaknesses has really propelled the development of more secure hash functions used in current blockchain technology.
SHA-2
Speaking of cryptographic hash functions used in blockchains, the SHA-2 is an improved version of SHA-1, which is more collision resistant. The SHA-2 also generates larger hash values (224 to 512 bits) and is more efficient than its predecessors as well. We can see the SHA-2 cryptographic hash function plays a more prominent role in blockchain technology.
Bitcoin is a network example that uses SHA-256 (a variant of SHA-2) in its PoW algorithm. SHA-256’s level of security and speed makes it suitable for verifying blockchain transactions and mining new blocks.
SHA-3
SHA-3 emerges as SHA-2’s successor, and it provides similar capabilities but uses a completely different internal design called Keccak. SHA-3 isn’t yet as widely adopted in blockchain technology, generally because SHA-2 is still considered secure and sufficient for most applications.
Because there is an ever-increasing demand for higher security levels in web3, more blockchain systems might begin adopting SHA-3.
Can Crypto Hash Be Decrypted?
At the time of writing, the answer is no. Cryptographic hash functions are meant to be one-way operations – they take input data and produce a hash, but they cannot be reverse-engineered to produce the original input data from the hash output.
While collisions (two different inputs producing the same hash value) are theoretically possible, but it would take an incredible amount of computational power. Therefore, in practice, a well-designed cryptographic hash function cannot be decrypted, providing a key aspect of data security.
Is Hash Safe?
Cryptographic hash functions are a valuable tool for cybersecurity, but like all security measures, they must be used properly and updated as needed to address new threats.
- Choose Strong Hash Functions: Cryptographic hashes that have strong collision resistance, such as SHA-256 or SHA-3.
- Avoid Weak Hash Functions: Avoid hash functions with known vulnerabilities like MD5 and SHA-1, which have been deemed unsafe for many applications and have been upgraded to SHA-2 and SHA-3 since.
- Ensure Secure Implementation: Use the hash function correctly, especially when storing sensitive data.
- Use Case Consideration: Consider the purpose of your hash function. Make sure it is strong enough for its intended use, whether that’s checking data integrity, securing a blockchain, or password storage.
- Stay Updated and Future-Proof: Keep track of new vulnerabilities that are discovered and advances in computing that could impact the security of the hash function. Be ready to switch to stronger cryptographic hashes if necessary.
- Regular Security Audits: Regularly review and audit your cryptographic hashes. This helps to identify weaknesses to ensure maximum security.
Which Types of Crypto Hash Are Used on Cryptocurrencies?
- Bitcoin: Uses SHA-256, a member of the SHA-2 family of cryptographic hash functions.
- Ethereum: Uses Ethash, a unique hash function designed specifically for Ethereum. It is specifically used to prevent the use of specialized mining hardware.
- Litecoin: Utilizes Scrypt, a password-based key derivation function great for deterring hardware-based attacks. It is also used as an alternative to SHA-256.
- Ripple (XRP): Uses SHA-512, a variant from the SHA-2 family of cryptographic hash functions, and then only extracts 256 bits to take up less space. This process is called “truncation”.
- Dogecoin: Similar to Litecoin, Dogecoin also uses Scrypt technology in its algorithm.
The Future of Cryptographic Hash
What does the future look like for crypto hashes? We predict it will be focused on maintaining robust security as technology changes. This means creating new hashes that can stand up against threats from powerful computers like quantum computers. Also, as more devices connect to the internet and blockchain technology improves, hashes will need to adapt. The ultimate goal is to find a balance between being secure, fast, and easy to use.
Conclusion
Cryptographic hash functions, or ‘crypto hashes’, are an integral part of digital security. They are used in password storage in web2 and have become a crucial part of web3 safety as well. They not only protect our data, but they also maintain the integrity of blockchains and also protect our identities online. As technology evolves so will crypto hashes so they can continually adapt to provide effective, efficient, and resilient defenses in the digital realm.
Related Articles
Multi-Signature Wallets – Are They Right for You?
Truncation in Cryptography: Privacy in the Digital Age
Trust VS Security in the Crypto World – Are They the Same?
0 comments